Managing network interfaces in pfSense can be somewhat confusing for a beginner.
Here we present the basic reminders and use cases for each type of interface.
There are 3 types of interface in pfSense:
- Physical interface: it corresponds to the physical interfaces of the server on which pfSense is running. These interfaces are usually named by their drivers like igb0, igb1, … for intel Gbps interfaces, or like re0, re1, … for Realtek interfaces.
- Virtual interface: these interfaces are created by pfSense and are associated with a service. For example, a virtual interface is automatically created when a VLAN or an OpenVPN server is configured.
- Logical interface: these are the interfaces that we can configure: IP address assignment, firewall filtering rules, … These interfaces are associated with a virtual or a physical interface.
Physical interfaces and virtual interfaces are called network ports.
A logical interface must be associated with a network port.
A network port (i.e. a physical interface or a virtual interface) can be associated whith only one logical (i.e. configurable) interface.
Physical interfaces on pfSense
A physical interface corresponds to a network interface card (i.e. NIC) of the pfSense server.
These interfaces are named according to their driver. For example: re0, re1, igb0, igb1, ath0, etc. They are identified by their MAC address.
A physical interface can be associated to a logical interface.
Thus, in the case of a pfSense with two interfaces (a LAN interface and a WAN interface), we could have the following association:
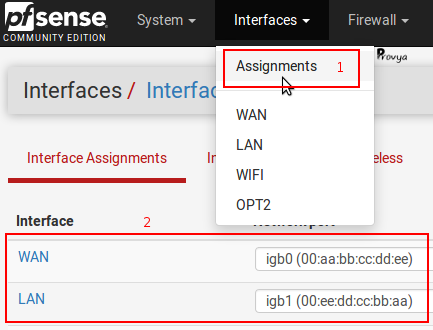
WAN [logical interface] = igb0 [physical interface]
LAN [logical interface] = igb1 [physical interface]
It is also possible to find or configure this association from the menu Interfaces > Assignments :
Virtual interfaces on pfSense
These interfaces are created when certain services (like VLAN, OpenVPN) are configured.
The configuration of an OpenVPN server automatically creates a virtual interface associated with this OpenVPN server instance. The virtual interface will be named ovpns1, ovpns2, etc…
This interface cannot be configured as is: it is only a network port. It is necessary to associate it with a logical interface in order to configure specific firewall or NAT rules on it.
When we proceed to this association, we obtain the following example:

In the above screenshot, we can see that the logical interface “OPT2” is associated with the virtual interface “ovpns1” which was created during the configuration of the OpenVPN server “VPN Provya“.
In the same way, the creation of a VLAN leads to the creation of a virtual interface (which will be named VLAN1, VLAN2, etc.).
This virtual interface will have to be associated with a logical interface in order to configure specific firewall or NAT rules on it.
Logical interfaces on pfSense
Logical interfaces are the configurable interfaces. These are the interfaces that we will be able to configure: associate an IP address; activate a DHCP server; configure firewall or NAT rules; etc.
Thus, when configuring a service (DHCP, OpenVPN, Captive Portal, etc.) the interfaces proposed will always be the logical interfaces.
The most common logical interfaces are LAN and WAN.
A logical interface is necessarily associated with a network port (i.e. a physical interface or a virtual interface).
Interface group
An interface group gathers several logical interfaces.
This group is a logical group to which we can apply firewall or NAT rules.
The use of an interface group is useful if we have several logical interfaces on which we want to apply exactly the same rules.
Thus, the firewall rules defined for this group will apply to all interfaces in the group.
The creation of an interface group is done from Interfaces > Assignments, “Interface Groups” tab:
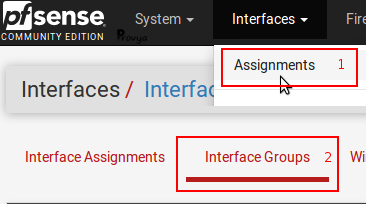
To add a new interface group, click on the “+Add” button.
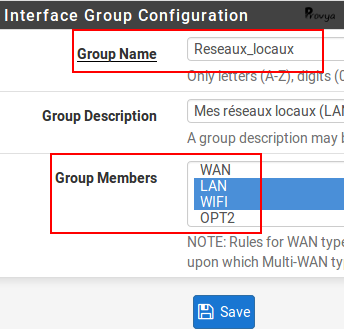
Fill the name of the interface group, a description (optional) and the list of the members of the group:
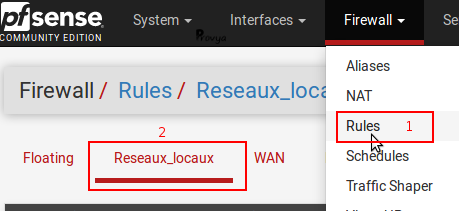
This interface group will be displayed in the firewall tab:
pfSense evaluates the rules configured on the interface group before checking the rules configured on the logical interface itself.
The firewall rules are checked in the following order:
- Floating rules
- Interface group rules
- Logical interface rules
Special case: OpenVPN
When configuring an OpenVPN server or client instance, a virtual interface is created (like ovpns1 or ovpnc1) and an interface group called “OpenVPN” is automatically created too.
The configurations made on this “OpenVPN” group apply to all OpenVPN services (i.e. all configured OpenVPN servers or clients).
If we want specific configuration per OpenVPN instance, then we need to create a logical interface for each existing OpenVPN virtual interface.
Use case
When configuring a service (DHCP, OpenVPN, Captive Portal, etc.) the available interfaces will always be the logical interfaces.
For services that can be configured for several interfaces (a firewall rule, for example), interface groups will also be displayed.
There are two special cases: the configuration of OpenVPN and IPsec clients or servers.
For these services, the choice of the interface will be :
- logical interfaces
- gateway groups
- VIP addresses
- localhost interface
- all existing logical interfaces (“any” choice)
Interface groups are not available.
Well done. We know everything we have to know to understand and properly configure services on the right network interface!
Related topics
[pfSense] Secure remote access for your home-office workers with OpenVPN
[pfSense] Configuring a Site-to-Site OpenVPN Instance



